15-Second summary Keeping up with Microsoft’s Patch Tuesday releases is time-consuming for analysts, who need to assess vulnerabilities quickly, determine…
Read More

15-Second summary Keeping up with Microsoft’s Patch Tuesday releases is time-consuming for analysts, who need to assess vulnerabilities quickly, determine…
Read More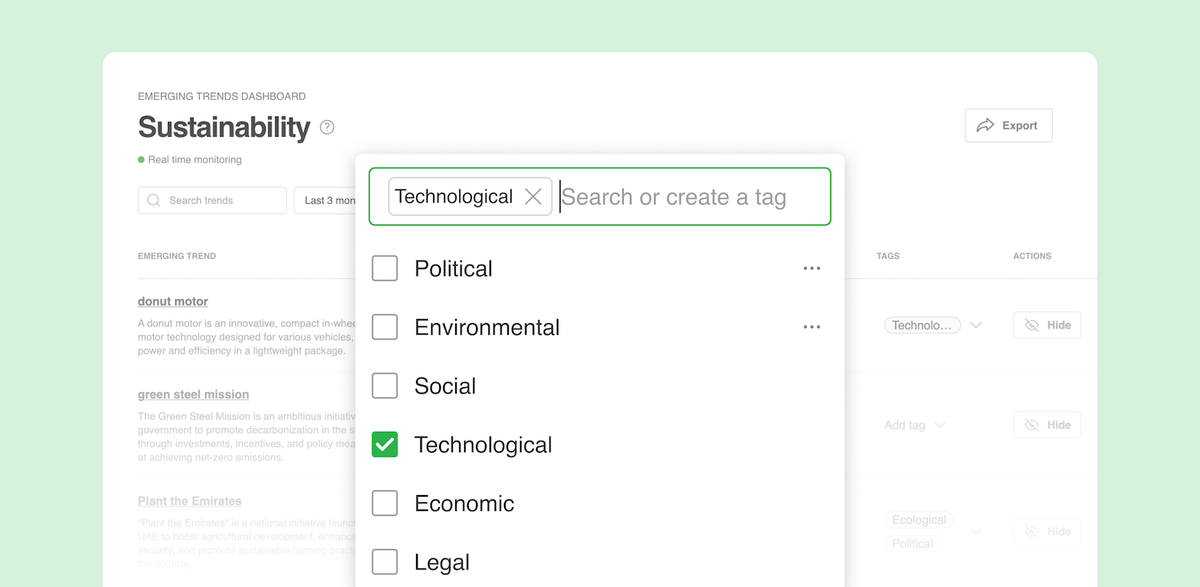
When conducting trend research, discovering new trends is only part of the challenge. Organizing, classifying, and tagging them ultimately makes…
Read More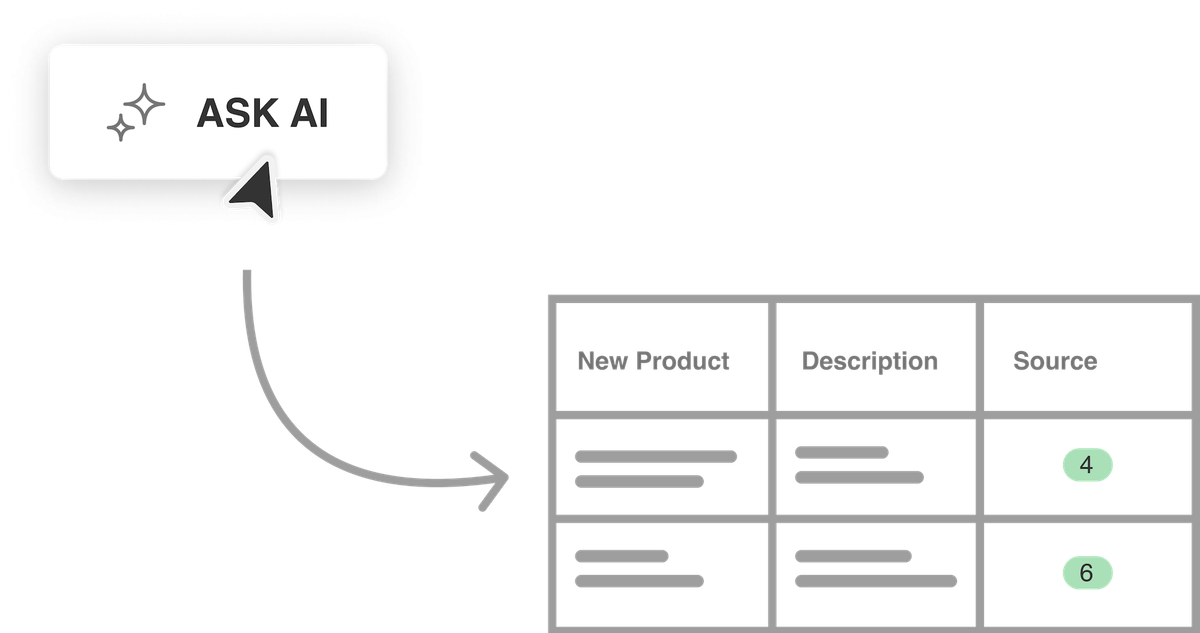
With Ask AI, Competitive Intelligence analysts can quickly extract and format critical product launches amongst their competitors into easily digestible…
Read More
15-sec summary Feedly’s integration with Anomali ThreatStream simplifies and accelerates threat intelligence workflows by directly delivering highly relevant intelligence into…
Read More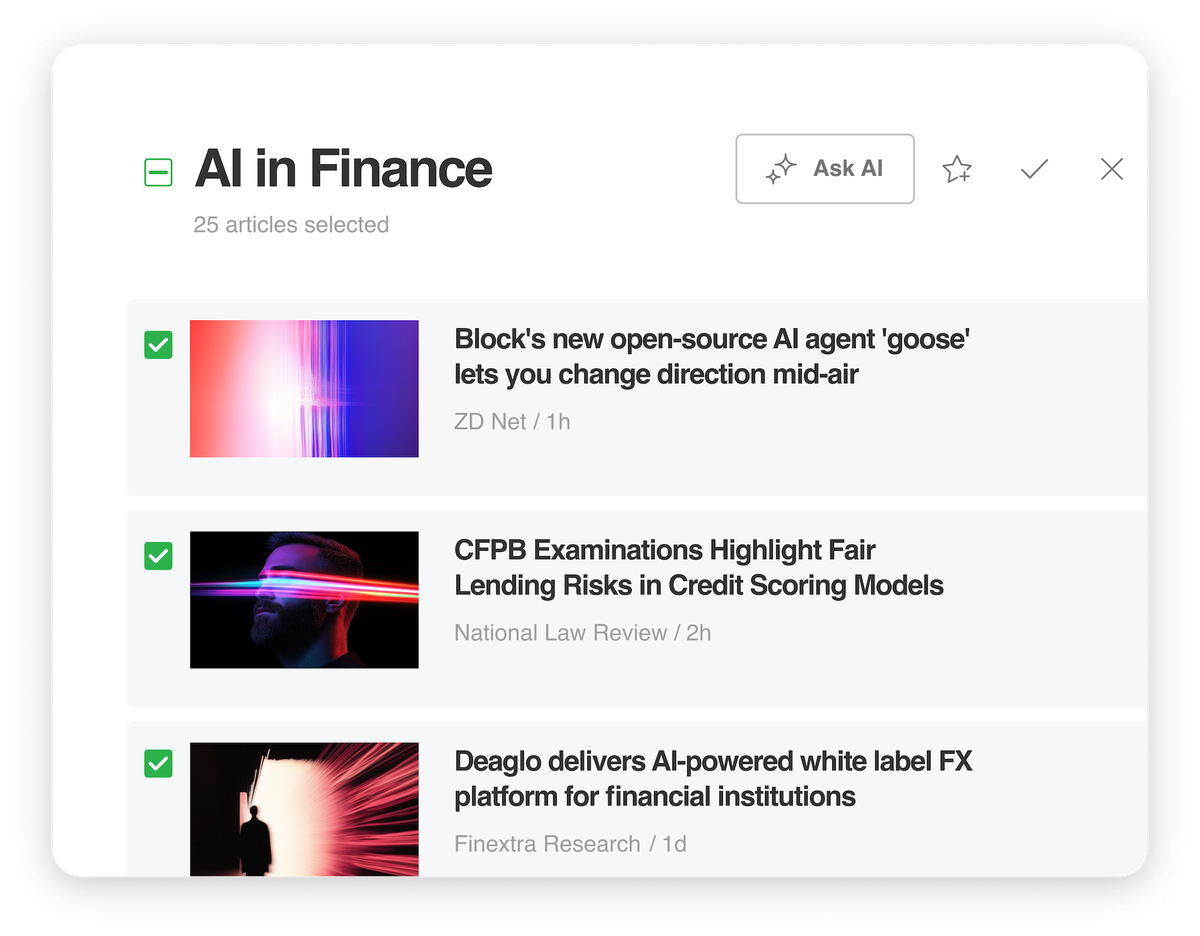
In this blog, we’ll explore three simple ways to bulk select articles and the actions you can perform with them.…
Read More
15-Second summary Bluesky is gaining traction as an alternative social media platform, partly because users have more control over the…
Read More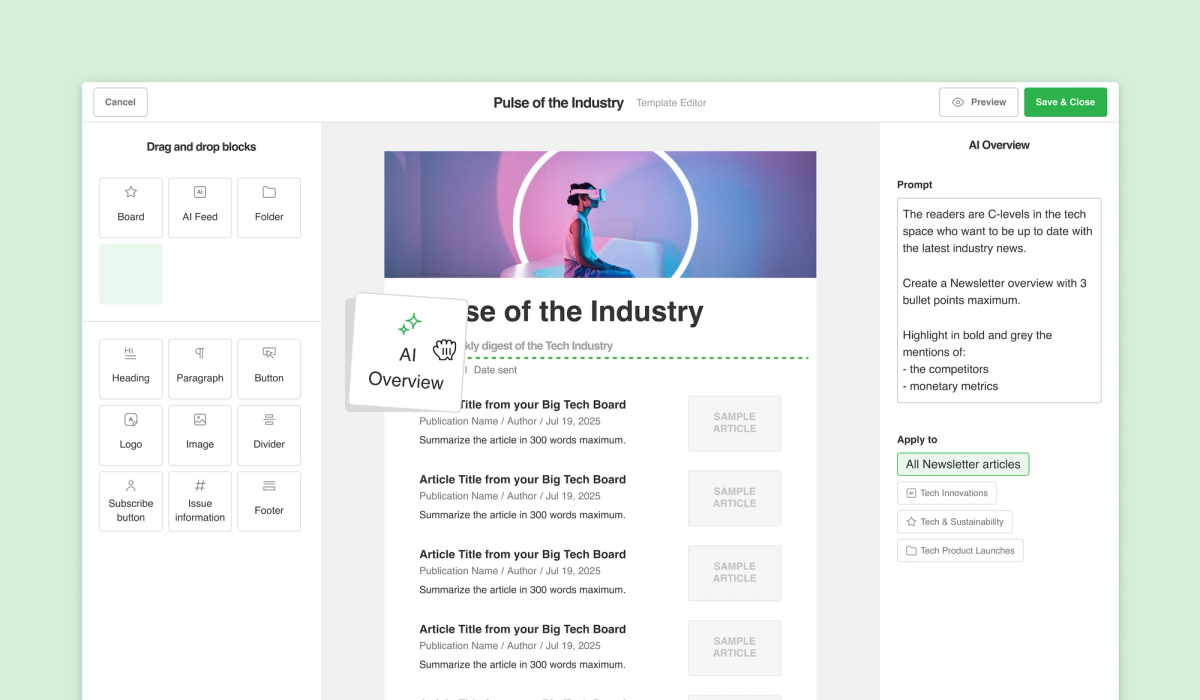
15-second summary Finding engaging content for your newsletter is only part of the challenge. You must also summarize key concepts,…
Read More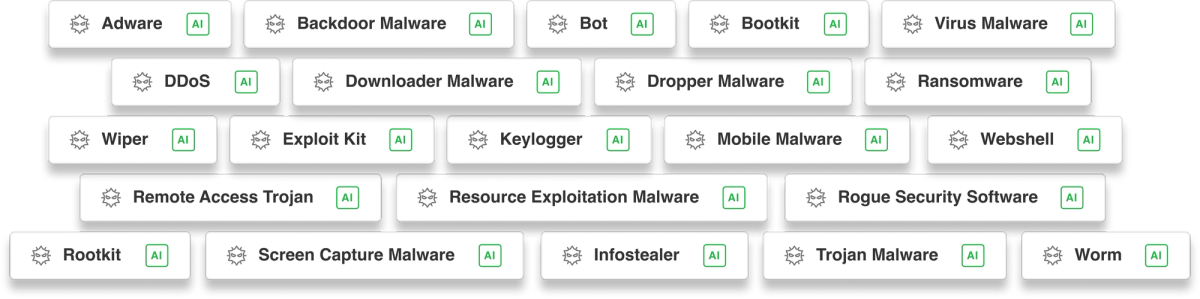
15-Second summary Malware categories often share common behaviors, such as ransomware encrypting files or botnets communicating with command-and-control servers. Feedly’s…
Read More
15-Second summary Change is hard, but these changes are worth it. We have revised the Feedly sidebar and eliminated the…
Read More
15-Second summary Creating threat intel newsletters involves more than collecting relevant information. You need to summarize key concepts, extract TTPs…
Read More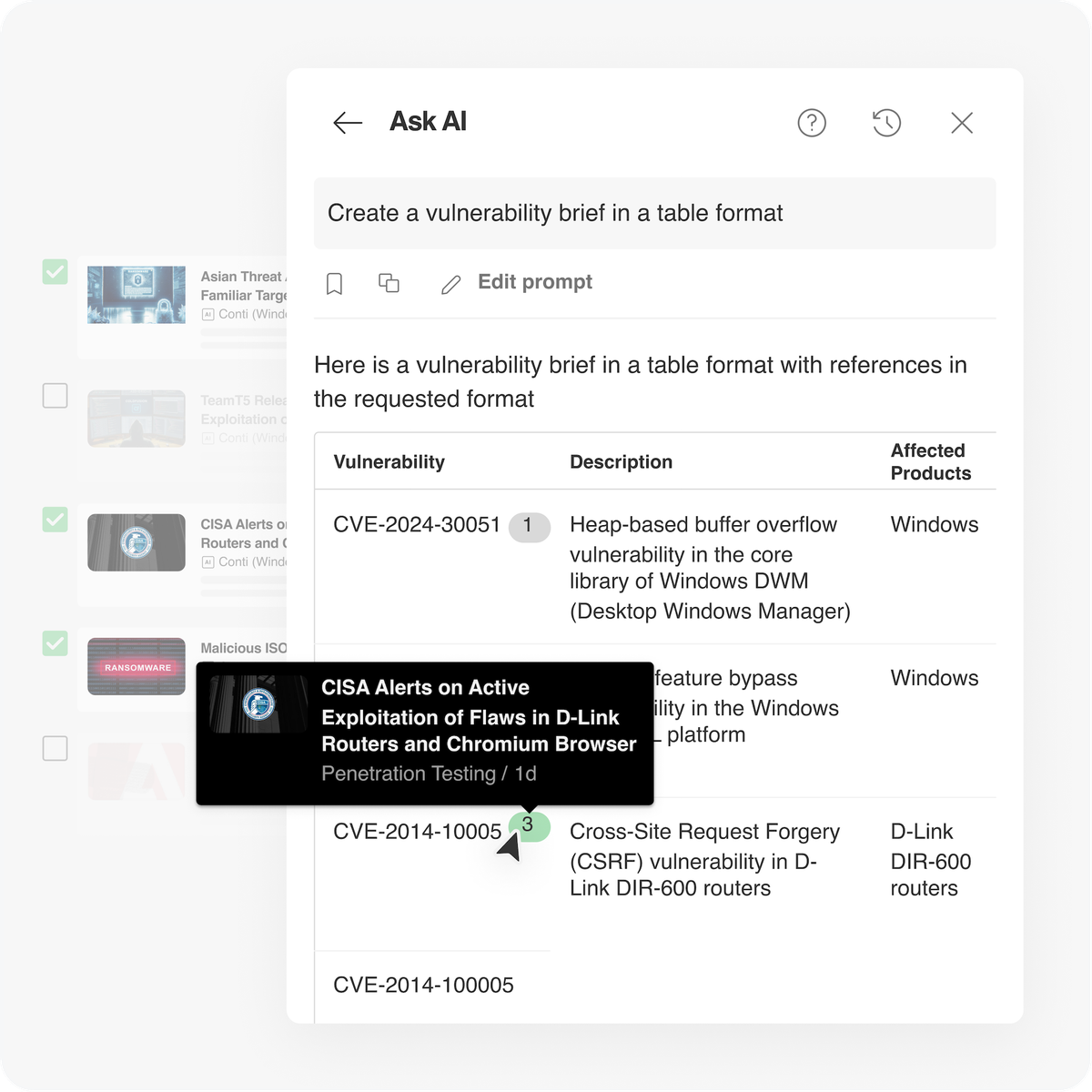
15-Second summary Reading through dozens of threat reports to understand a campaign or identify emerging TTPs can eat hours of…
Read More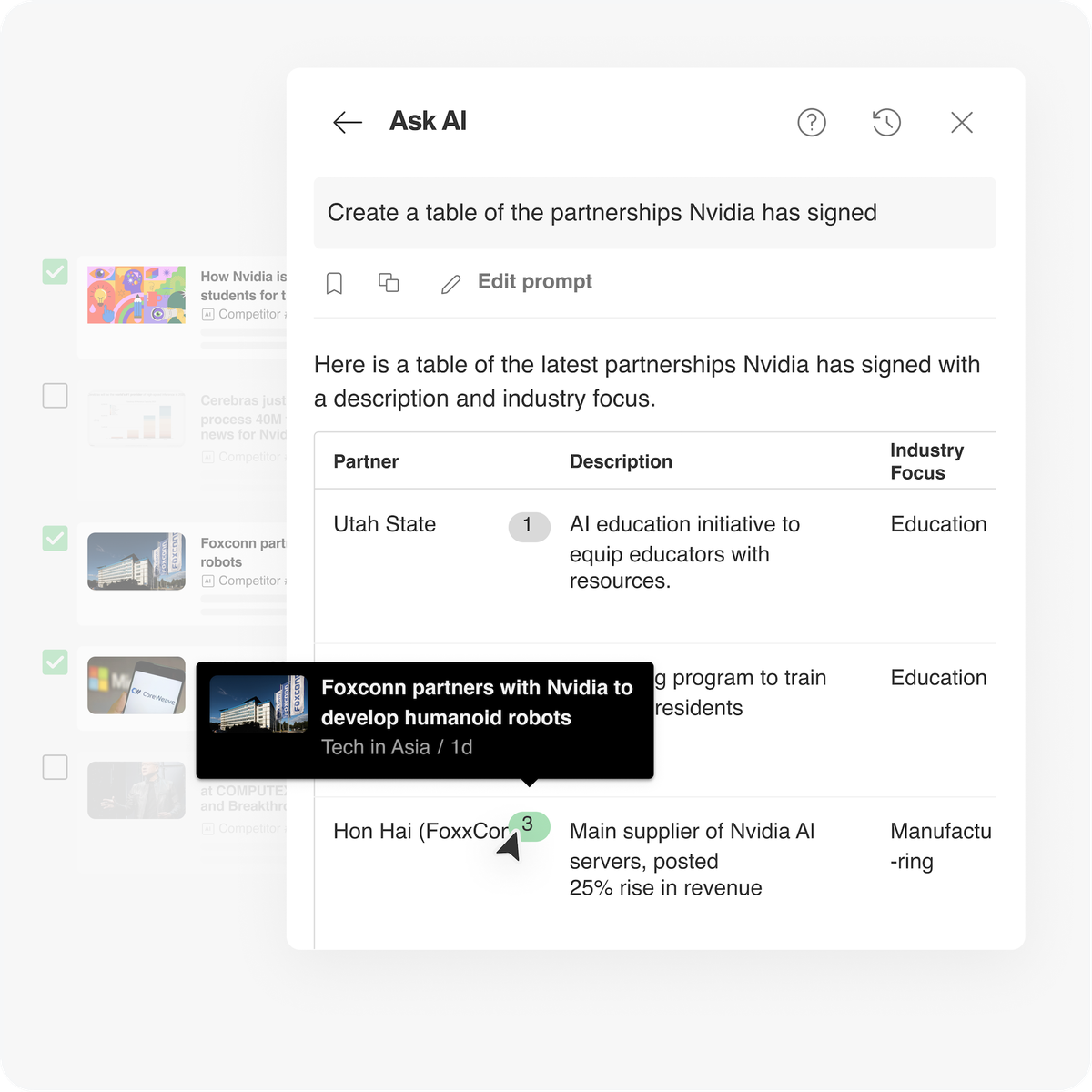
15-Second summary Reading through the news to track competitor moves, emerging technologies, and regulatory changes can take hours every day—leaving…
Read More
15-Second summary Feedly AI Feeds are already powerful, but what if you could fine-tune them even further? Introducing Natural Language…
Read More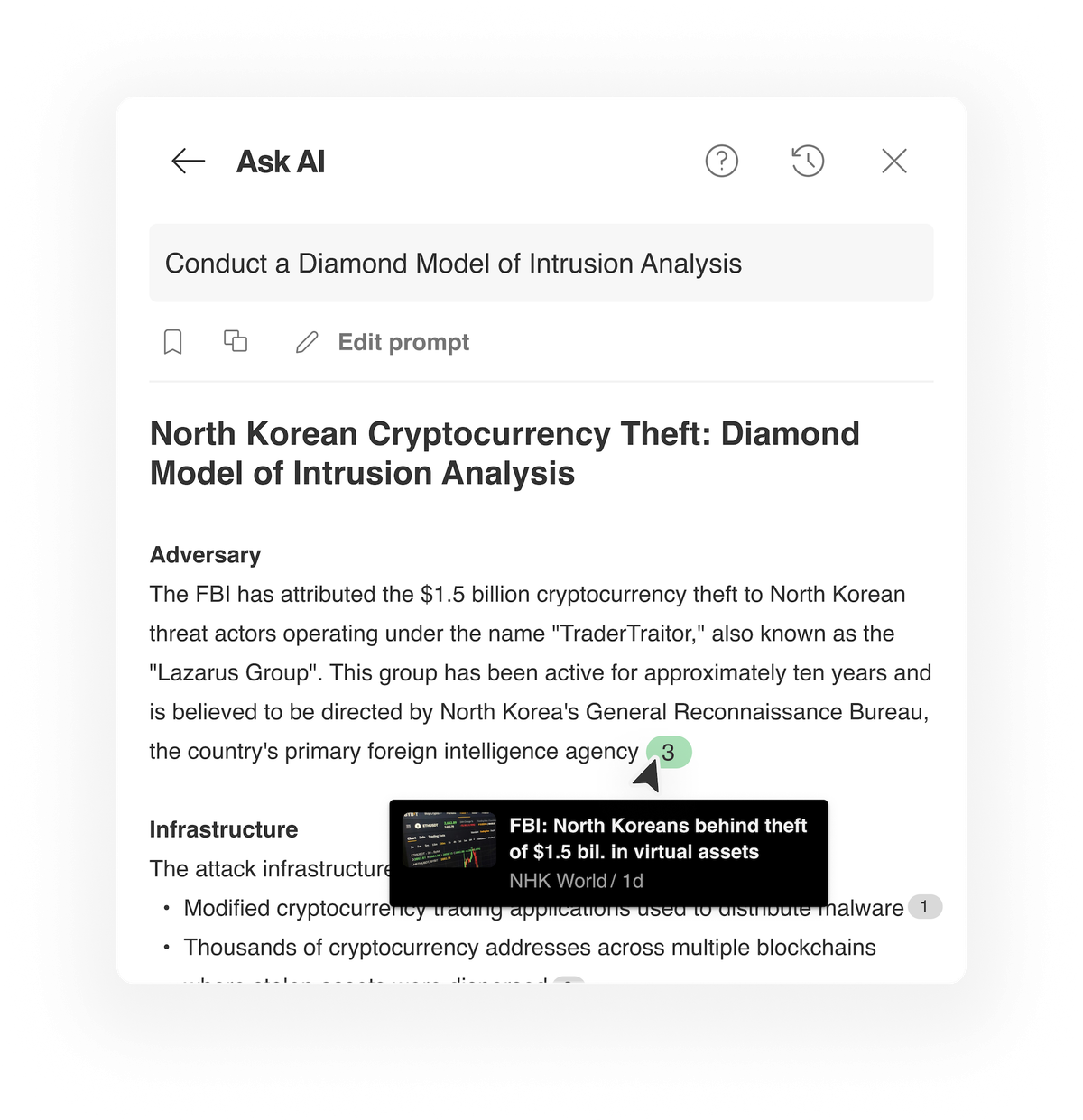
The Diamond Model of Intrusion Analysis is a widely used framework in cybersecurity to analyze adversary behaviors, infrastructure, and victimology…
Read More