Visit Our websites
Overview
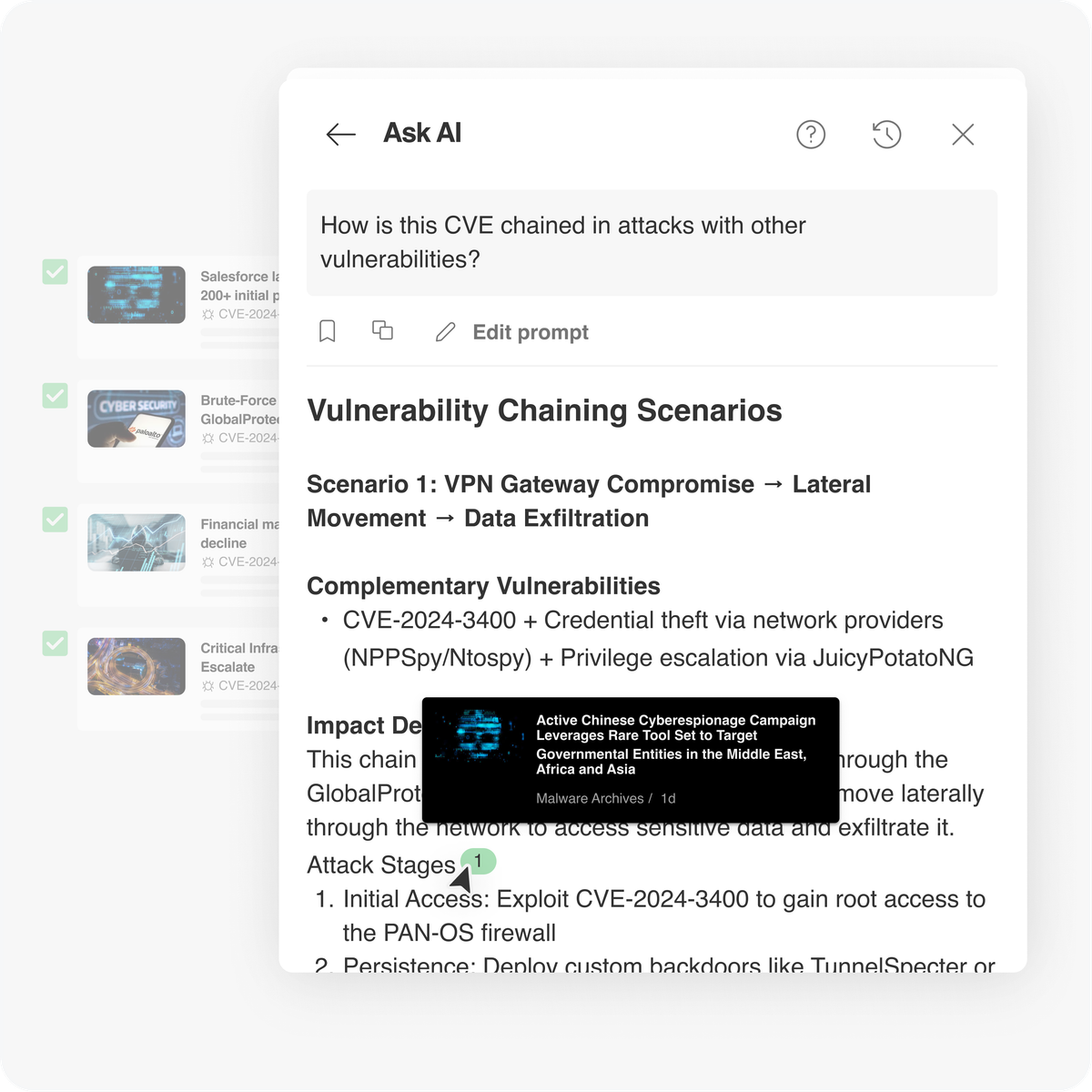
One vulnerability might not bring your organization down, but when chained with others, it can create critical risks, often catching defenders off guard. At Feedly, we built CVE Insights Cards to give you a complete view of critical vulnerabilities. Now, with Ask AI in CVE Insights Cards, CTI teams can dive even deeper: asking targeted questions around specific CVEs, exploring their chaining potential, and identifying hidden exploitation paths, which is exactly what this new prompt is designed to help you uncover.
This Ask AI Prompt generates detailed scenarios showing how a CVE could be chained with complementary vulnerabilities, outlines the impact of potential attack paths, maps the stages where chaining could occur, and highlights related threat actor TTPs in a structured format. It’s built to help you spot attack chains others might miss, strengthen your defenses before threat actors make their move, and stay one step ahead in a constantly evolving threat landscape.
You can save your prompt in the Ask AI library and re-run it against other CVEs to see consistent output.
Ask AI Prompt
Copy and paste this prompt directly in your Ask AI panel!
Provide a short overview of this CVE.
Give me chaining scenarios for this vulnerability, each of the scenarios with:
1. Complementary vulnerabilities that could be chained with this CVE to achieve greater impact.
2. A description of the impact of the chained attack (e.g., privilege escalation, lateral movement, remote code execution, data exfiltration).
3. An outline on the attack stages where chaining would occur (e.g., initial access, persistence, escalation).
4. Any known threat actor TTPs (Tactics, Techniques, and Procedures) that align with this chaining potential, in a table format.
5. An attack chain diagram that visually shows how the CVE could be exploited within the chained attack path.
6. Provide log sources and specific details that could aid in the detection of these scenarios
7. Any detection rules that may already exist
8. Providing details if the chain is theoretical or has already occurred. Ask AI Response
Where is the information coming from?
Hover over the numbered bubbles in the Ask AI Response to view the exact article from which the information came.
In short…
Start using this prompt in Ask AI to go beyond surface-level analysis and uncover how attackers might chain vulnerabilities to compromise your environment. It’s a powerful way to turn CVE data into real-world defensive strategies.
Try Ask AI in CVE Insights Cards
Spot potential vulnerability chains before attackers do.

BONUS LINK VISIT NOW
Visit Our websites