Columbia Student’s Cheating Tool Raises $5.3M. A headline that’s sparking controversy in both tech and education industries alike. This disruptive…
Read More

Columbia Student’s Cheating Tool Raises $5.3M. A headline that’s sparking controversy in both tech and education industries alike. This disruptive…
Read More
AI Revolution: Ending Disease and Abundance AI Revolution: Ending Disease and Abundance isn’t just a catchy phrase—it’s becoming one of…
Read More
AI Creates Innovative Tools to Explore Cosmos—this groundbreaking shift is capturing the attention of scientists and space enthusiasts alike. Are…
Read More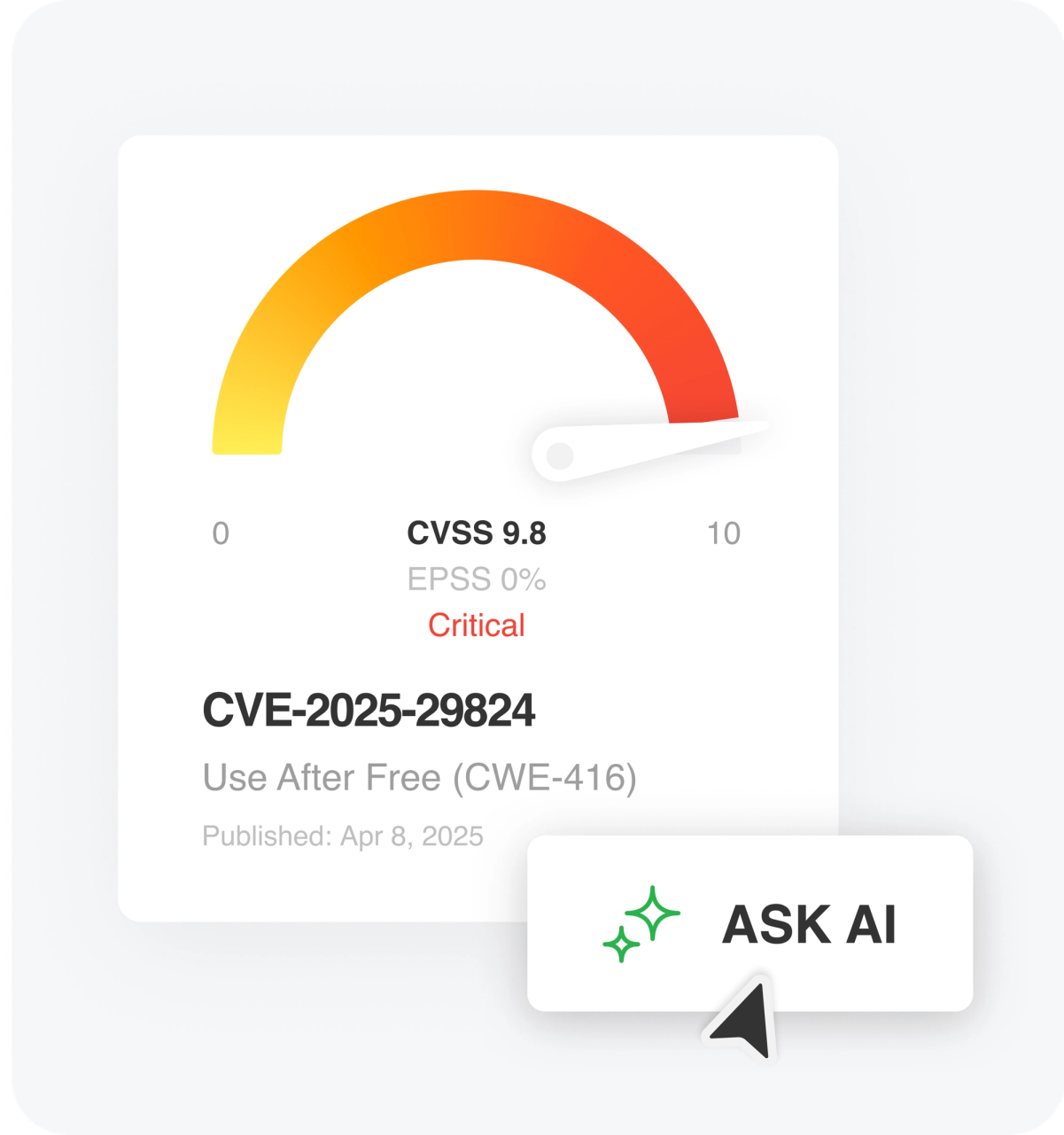
15-Second summary Assessing the real-world risk of a CVE can be time-consuming and fragmented. CVE Insights Cards provide a 360°…
Read More
Full Economic Automation: AI Job Threats Full Economic Automation: AI Job Threats has emerged as a pressing topic as artificial…
Read More
Future of AI Insights from Tech Visionary The Future of AI Insights from Tech Visionary sparks both curiosity and debate,…
Read More
AI vs. Grammar Pedants: Where Do You Stand? AI vs. Grammar Pedants: Where Do You Stand? This question isn’t just…
Read More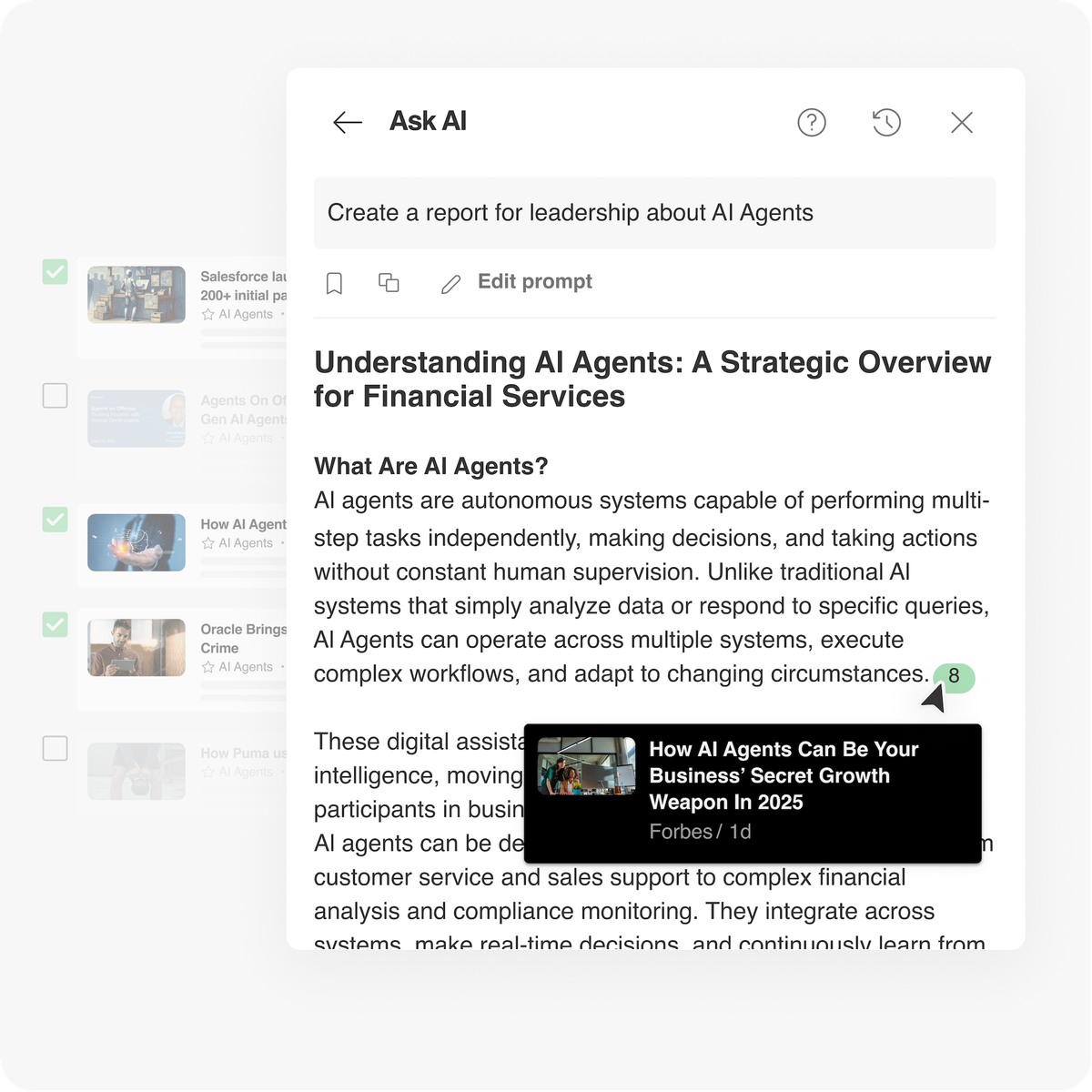
Overview AI agents are everywhere in the headlines—but for many professionals, especially in complex industries like financial services, the real…
Read More
ChatGPT’s Enhanced Memory: What You Need to Know If you’ve ever wondered how ChatGPT can carry on a conversation or…
Read More
Revolutionary Graphene Flash Memory Achieves 400 Picosecond Writes Revolutionary Graphene Flash Memory Achieves 400 Picosecond Writes — a breakthrough pushing…
Read More
Artisan’s $25 Million Funding for AI Agents Artisan’s $25 Million Funding for AI Agents has sent waves through the tech…
Read More
Introduction In today’s rapidly evolving AI landscape, where automation is king and machine learning powers everything from personalized shopping to…
Read More
Embracing Creativity in an AI-Driven World Embracing Creativity in an AI-Driven World is no longer a futuristic concept — it’s…
Read More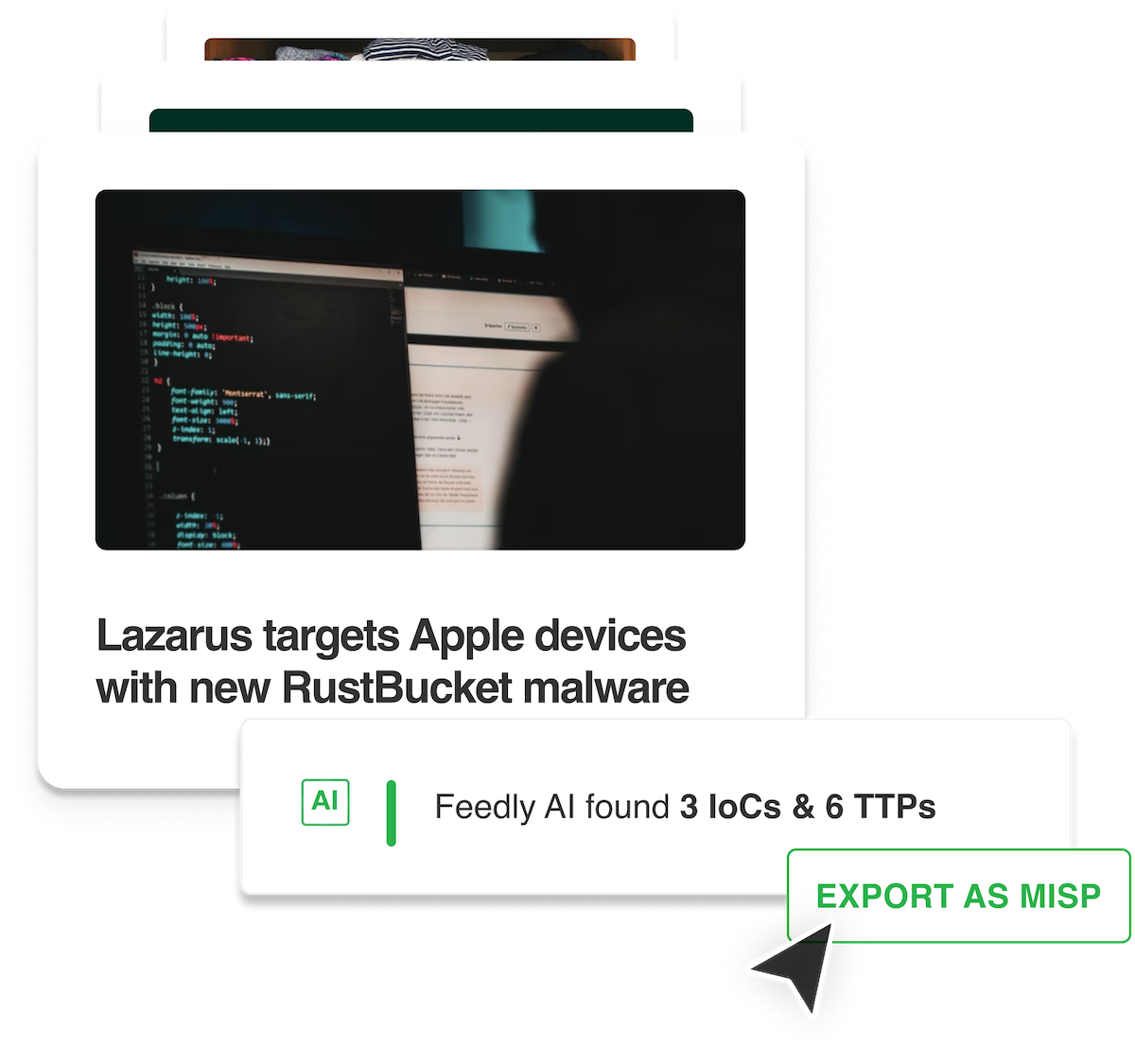
15-second summary MISP is a powerful platform for storing and distributing cyber threat intelligence, including indicators of compromise (IoCs). However,…
Read More